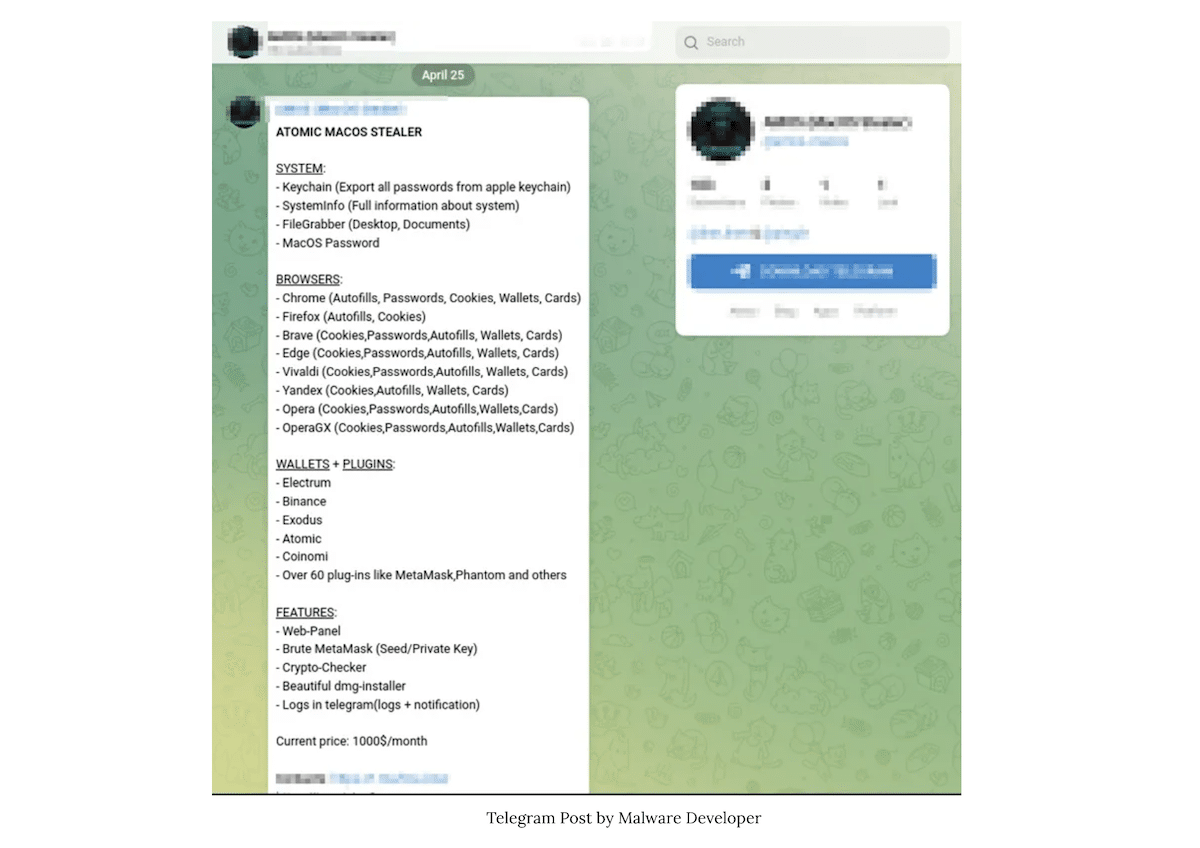
Cyble Research and Intelligence Labs (CRIL) has discovered a new macOS malware, Atomic macOS Stealer (AMOS) being sold on Telegram for $1000 per month. The malware is designed to extract confidential information from the computer like Keychain passwords, auto-fills, wallets, credit card information, and more.
Recently, Elastic security labs stated that macOS significantly was more secure than Windows and Linux in its 2023 Global Threat Report Spring with only 6% of malware detected in opposition to 54% on Linux and 39% on Windows of all instances.
However, the report also mentioned that crypto-miners were the most dominant macOS malware, XMRig accounted for nearly 40% of instances. The new AMOS macOS malware can also target cryptowallets.
AMOS macOS malware also targets cryptowallets like Exodus, Binance, and others
According to CRIL’s findings, viewed by Cyble, the Threat Actor (TA) behind the AMOS is continuously upgrading the malware to add new capabilities, its latest update was released on April 25.
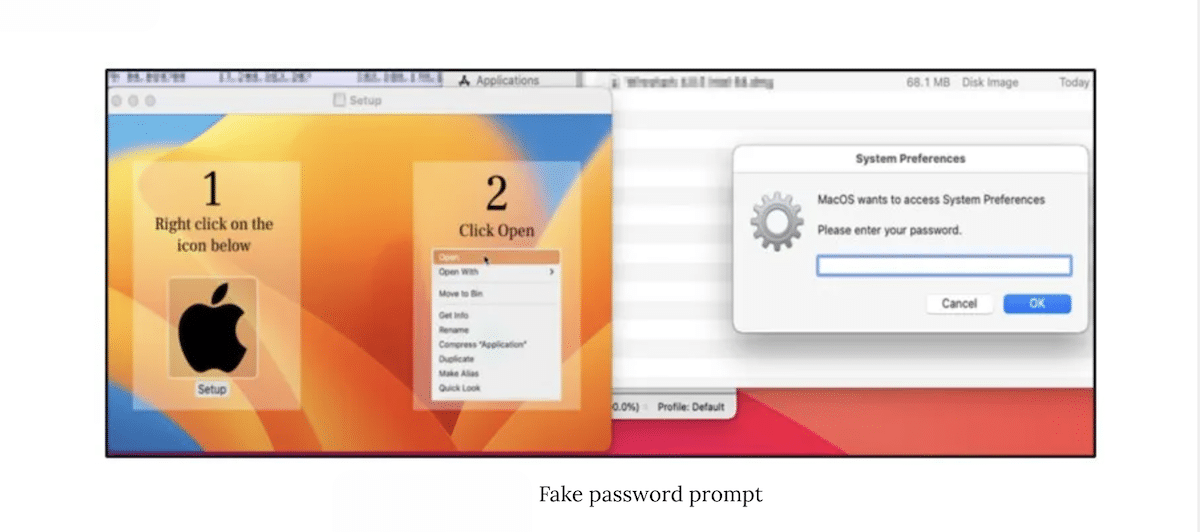
AMOS displays a fake prompt to extract the machine’s password and beings to target the Keychain (password management tool), cryptowallets, browser(s) directories, files, and system information to collect sensitive information like complete system information, passwords, credit cards details, and others. The data is sent to a remote C&C server.
The Atomic macOS Stealer can steal various types of information from the victim’s machine, including keychain passwords, complete system information, files from the desktop and documents folder, and even the macOS password. The stealer is designed to target multiple browsers and can extract auto-fills, passwords, cookies, wallets, and credit card information. Specifically, AMOS can target cryptowallets such as Electrum, Binance, Exodus, Atomic, and Coinomi.
TA also offers additional services to its customers like a web panel for managing victims, a crypto checker, private keys, meta mask brute-forcing, and others in the $1000 monthly subscription fee.
Such malware is installed on the machines by exploiting vulnerabilities or hosting on phishing websites. Therefore, Mac users are advised to download apps from the official Apple App Store, use antivirus, keep strong passwords and 2FA, enable biometric security authentication feature, do not open dubious links receive in emails, and update their device to the latest OS regularly.