The presence of Bluetooth technology in our modern devices has revolutionized the way we connect and interact with the world around us. However, this widespread adoption also brings with it the potential for security vulnerabilities.
Researchers at the French research center EURECOM recently unveiled a new Bluetooth vulnerability named BLUFFS (Bluetooth Forward and Future Secrecy) that poses a significant threat to a wide range of devices, including iPhones.
New Bluetooth flaw, BLUFFS, enables attackers to spy on communications and alter data
BLUFFS encompasses six distinct exploits that target the fundamental architectural level of Bluetooth, making them effective against various devices and operating systems. iPhones running Bluetooth versions 4.1 to 5.4, encompassing all models from the iPhone 6 to the latest iPhone 15, are particularly vulnerable to at least three of these attacks.
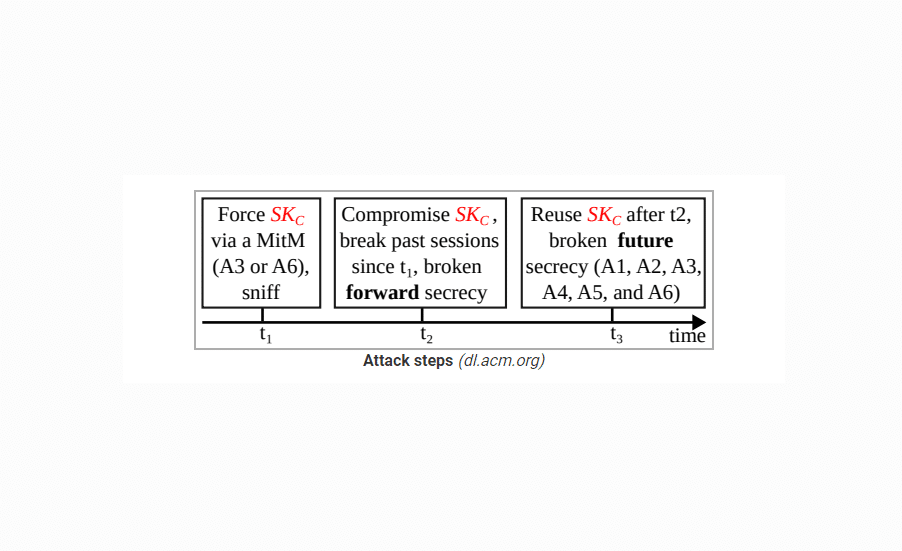
The central point of the vulnerability lies in two previously unknown flaws within the Bluetooth standard, specifically affecting the unilateral and repeatable session key derivation process. BLUFFS manipulates this process, enabling attackers to compromise the forward and future secrecy guarantees of Bluetooth’s pairing and session establishment security mechanisms.
Attack mechanism
BLUFFS exploits the session key derivation process to force the generation of a weak and predictable session key. Attackers can then brute-force this key, granting them the ability to decrypt past communications and manipulate future ones. The attack scenario assumes that an attacker is within Bluetooth range of two victim devices, allowing them to capture packets in plaintext, negotiate a weak session key, and impersonate one device to the other.
Impact and implications
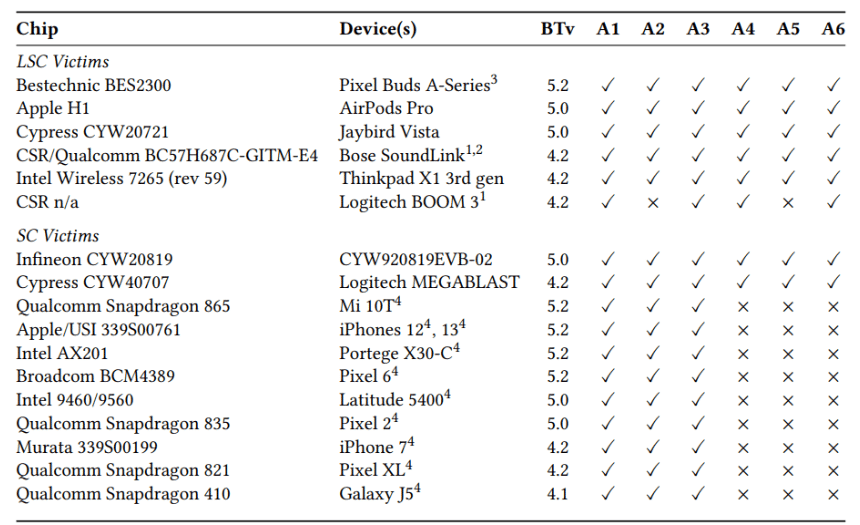
The widespread adoption of Bluetooth technology, coupled with the architectural level of these vulnerabilities, raises significant concerns for the entire Bluetooth ecosystem. EURECOM researchers tested BLUFFS against 17 different Bluetooth chips and found all devices susceptible to the attacks. The impact extends to a vast array of devices, including smartphones, earphones, laptops, and more.
Recommendations
To counter BLUFFS attacks, EURECOM researchers have proposed an enhanced Bluetooth session key derivation function. This solution, which maintains backward compatibility with the Bluetooth standard, aims to minimize overhead while preventing the exploitation of the identified vulnerabilities.
Additionally, the Bluetooth Special Interest Group (SIG), responsible for overseeing the Bluetooth standard, has acknowledged the severity of BLUFFS attacks and recommends implementing solutions that reject service-level connections with weak keys. They also advise using ‘Security Mode 4 Level 4’ for higher encryption strength and operating in ‘Secure Connections Only’ mode during pairing.
Suggestions for iPhone users
Given the integration of Bluetooth into the Apple ecosystem, iPhone users are urged to stay informed about security updates and patches released by Apple. While there is no immediate fix available for users, remaining vigilant and following recommended practices, such as turning off Bluetooth when not in use and avoiding connections with unknown devices, can help minimize potential risks.
(via Bleeping Computer)
Read more: