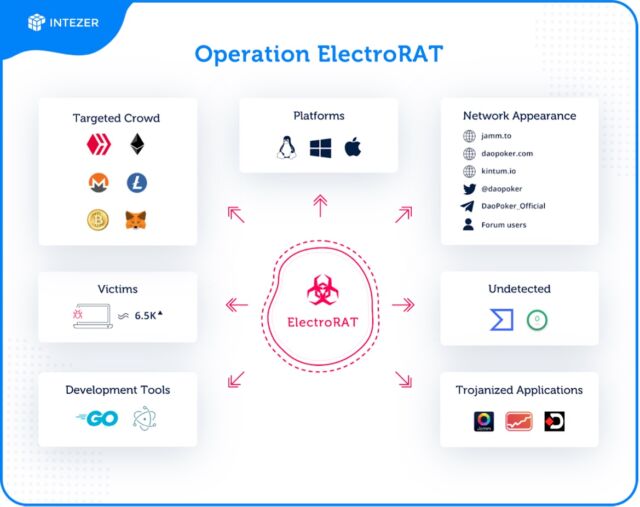
A new report published by a security firm says that a ring of criminals has tried to join the cryptocurrency market via a wide-ranging operation. The operation consists of a full-fledged marketing campaign, custom cryptocurrency-related applications, and a new Remote Access Tool (ElectroRAT) written from scratch.
Rising cryptocurrency valuations have broken record after record in the last few years, turning people with economical holdings into overnight millionaires. Now a group of criminals is looking to get rich at the expense of other people. The campaign includes trojanized applications, fake social media accounts, domain registrations, websites, and a tool called ElectroRAT.

ElectroRAT code used to target multiple operating systems
The report was published by Intezer, a security firm, saying that the operation has been active since last January at least. The operation relies on a network of social media profiles, fake companies, and websites to win the trust of potential victims.
The apps pose as typical software that is useful to cryptocurrency holders. Inside the apps, there is remote access hidden that is written from scratch. Once an app is installed, ElectroRAT allows the crooks to take screenshots, upload, download, and install files, log keystrokes, and administer commands on infected devices.
It is rather common to see various information stealers trying to collect private keys to access victims’ wallets. However, it is rare to see tools written from scratch and used to target multiple operating systems for these purposes.
The attacker behind this operation has lured cryptocurrency users to download trojanized applications by promoting them in dedicated online forums and on social media. We estimate this campaign has already infected thousands of victims—based on the number of unique visitors to the pastebin pages used to locate the command and control servers.
ElectroRAT uses Pastebin pages published by a user name Execmac to locate its command-and-control server. Since January 2020, the pages have received more than 6,700 views. Intezer believes that the number of page visits matches the number of people infected.
There were three apps found that were corrupted to infect targets were called DaoPoker, eTrade, and Jamm. The first app is a poker that grants bets with cryptocurrency. The latter apps claimed to be a cryptocurrency trading platform.
The post by Intezar also provides links that Linux and Windows users can use to find ElectroRAT running in memory if they suspect their device harbor the malware. Individuals impacted by the malware should change all passwords and move funds to a new wallet.
Read Also: