Apple’s Find My network is a pretty helpful feature for users within the tech giant’s ecosystem. The anonymous and encrypted network is a great way to track devices – even if the devices do not have access to Wi-Fi. However, a new report that claims the network can also be used to send messages and other data.
According to an in-depth blog post by security researcher Fabian Bräunlein, Apple’s Find My network can be exploited to send messages and other data. The research was able to discover a way to turn the network into a data transfer mechanism with the help of local devices to upload that data.
Apple’s Find My network exploited by security researcher
Apple’s Find My network is designed to utilize the active iOS base, which is made up of hundreds of millions of Apple devices, to serve as individual nodes that can transfer location data. The functionality can help users locate their AirTags as well as other lost or stolen Apple devices.
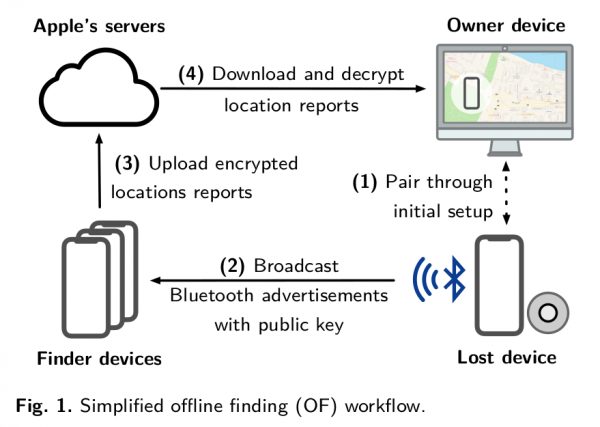
Bräunlein reveals that it is not only possible to imitate the way AirTag connects to the Find My network but also transmit its location. AirTag sends its location through an encrypted broadcast so when this location data is replaced with a message, it is concealed by the broadcast’s encryption. The researcher included a simplified demonstration of how the functionality works.
1. When paring an AirTag with an Apple Device, an Elliptic Curve key pair is generated and the public key is pushed to the AirTag (and a shared secret to generate rolling public keys)
2. Every 2 seconds, the AirTag sends a Bluetooth Low Energy broadcast with the public key as content (changes every 15 minute deterministically using the previously shared secret)
3. Nearby iPhones, Macbooks, etc. recognize the Find My broadcast, retrieve their current location, encrypt the location with the broadcasted public key (using ECIES) and upload the encrypted location report
4. During device search, the paired Owner Device generates the list of the rolling public keys that the AirTag would have used in the last days and queries an Apple service for their SHA256 hashes. The Apple backend returns the encrypted location reports for the requested key ids
5. The Owner Device decrypts the location reports and shows an approximate location
Currently, any security implications regarding this discovery are unknown. Since this is technically an exploit, it could be used maliciously in the future. On the other hand, Apple could end up developing this into a feature for users in the future.
In similar news, a German security researcher recently hacked an AirTag and modified its Near Field Communication (NFC). The researcher found the SoftDevice firmware used in the item tracker and was able to break into the tracker’s firmware and reprogram its software in 2 hours. Despite his success, the hacker has stated that the process was not easy and admitted to bricking two AirTags in the process.
1 comment