A German security researcher @stacksmashing hacked an AirTag and modified its Near Field Communication (NFC). Through reverse engineering, the researcher broke into the tracker’s firmware and reprogram its software. Having said that, the hacker admits that it was not easy and he bricked two AirTags in the process.
Yesss!!! After hours of trying (and bricking 2 AirTags) I managed to break into the microcontroller of the AirTag! 🥳🥳🥳
/cc @colinoflynn @LennertWo pic.twitter.com/zGALc2S2Ph
— stacksmashing (@ghidraninja) May 8, 2021
NFC technology enables users to securely make transactions, exchange digital content, and connect electronic devices via touch. These transmissions are short-range, therefore, they require the devices to be close proximity (touch or few centimeters apart).
Hacker changes AirTag NFC instruction
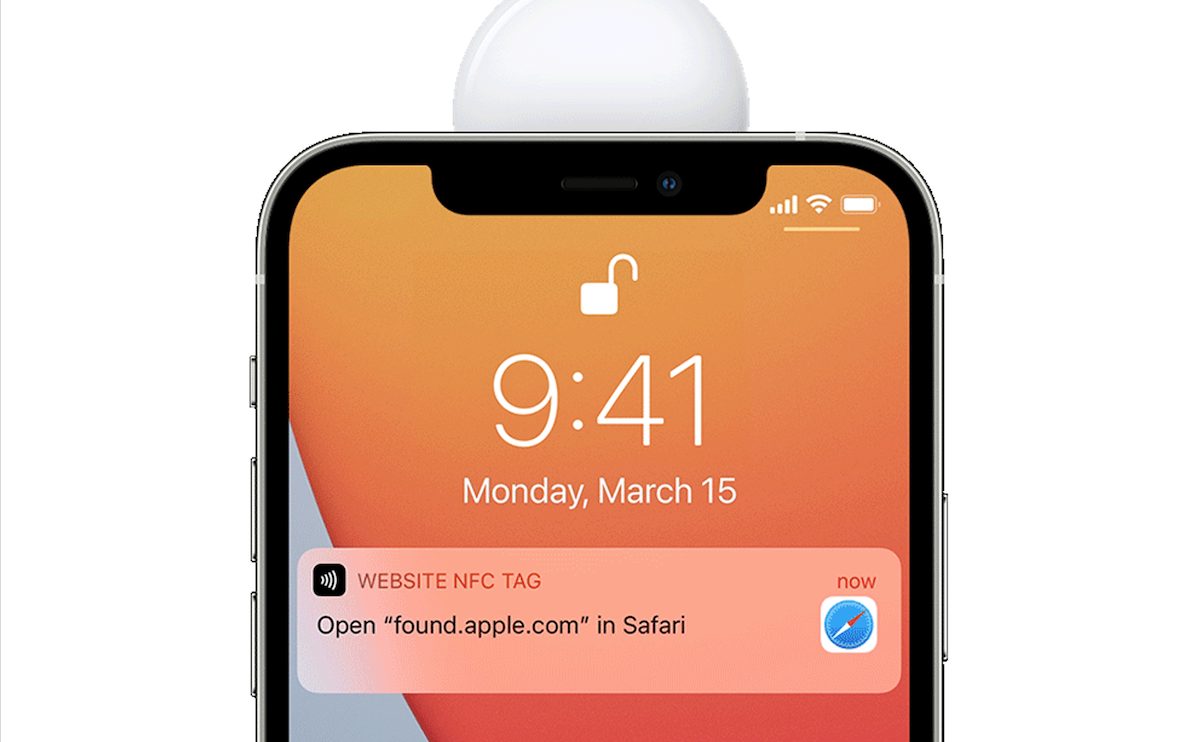
Apple uses NFC technology to detect and disable unknown trackers. The company explains that “if a user detects an unknown AirTag, they can tap it with their iPhone or NFC-capable device and instructions will guide them to disable the unknown AirTag” and “will display a contact phone number for the owner if they have provided one” by directing the user to found.apple.com. But in control of AirTag’s NFC URL, the hacker was able to show his website or a YouTube video, when a modified tracker was scanned via an iPhone.
Built a quick demo: AirTag with modified NFC URL 😎
(Cables only used for power) pic.twitter.com/DrMIK49Tu0
— stacksmashing (@ghidraninja) May 8, 2021
As shared on Twitter, @stacksmashing found the SoftDevice firmware used in the tracker and was able to successfully break in the software after 2 hours. He wrote that this experiment “confirmed that we can re-flash the microcontroller! Woohoo.”
It an interesting situation where an Apple device has been hacked by reverse-engineering its IC (Integrated Chip controller), which is the brain of an electronic device. And with the ability to change the IC programming, the hacker might be able to change other functions of the tracker as well like changing its sound, battery percentage, and others.
Since its launch, issues regarding AirTag security are reported. A recent review highlighted that “it is frighteningly easy to stalk” an AirTag by evading Apple’s security measures, especially by an abusive partner or miscreant.
I got multiple alerts: from the hidden AirTag and on my iPhone. But it wasn’t hard to find ways an abusive partner could circumvent Apple’s systems. To name one: The audible alarm only rang after three days — and then it turned out to be just 15 seconds of light chirping. And another: While an iPhone alerted me that an unknown AirTag was moving with me, similar warnings aren’t available for the roughly half of Americans who use Android phones.
Apple has done more to combat stalking than small tracking-device competitors like Tile, which so far has done nothing. But AirTags show how even Apple, a company known for emphasizing security and privacy, can struggle to understand all the risks involved in creating tech that puts everyday things online.
And this latest discovery heightens security concerns regarding Apple’s compact tracker.
1 comment
Comments are closed.