Back in August, a cyber security researcher found a flaw in iOS VPN apps that failed to close a VPN tunnel and therefore, leaked user data. Now, another security researcher has discovered a second flaw in VPN apps on iOS.
iOS 16 communicates with Apple services outside of an active iOS VPN tunnel
To understand the flaws discovered in iOS VPN apps, it is important to know how VPNs operate. A Virtual Private Network (VPN) creates a new public IP address and DNS server for a device and sends data to the server. When a flaw exists within a VPN, this connection exposes users’ unencrypted data like their IP address to ISPs and other parties, even when active.
The first issue was discovered by a cyber security researcher, Micheal Horowitz, who claimed that iOS VPN apps fail to close VPN tunnels after the connection has ended and allegedly leak user data. According to Horowitz, the flaw has existed since 2020.
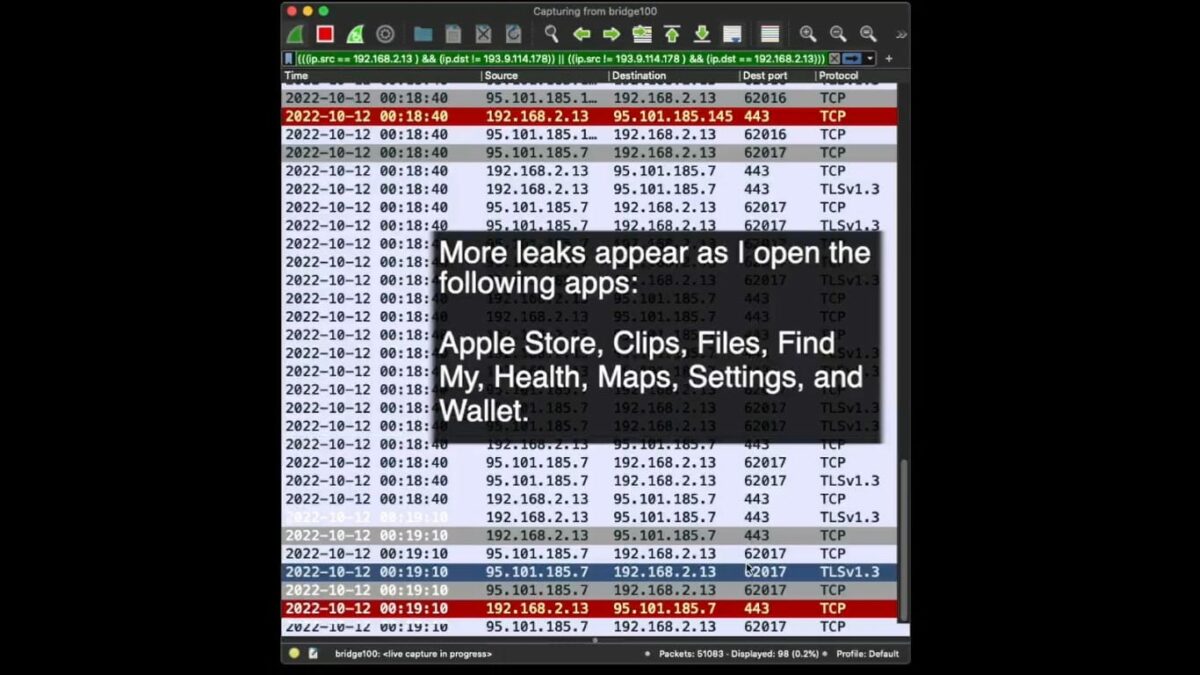
The latest development comes from developer and security researcher Tommy Mysk who ran some tests and discovered that IP addresses can be accessed even when a VPN is active. In addition, Mysk discovered that several stock iOS apps ignore the VPN tunnel and communicate directly with Apple services.
We confirm that iOS 16 does communicate with Apple services outside an active VPN tunnel. Worse, it leaks DNS requests. #Apple services that escape the VPN connection include Health, Maps, Wallet.
We confirm that iOS 16 does communicate with Apple services outside an active VPN tunnel. Worse, it leaks DNS requests. #Apple services that escape the VPN connection include Health, Maps, Wallet.
We used @ProtonVPN and #Wireshark. Details in the video:#CyberSecurity #Privacy pic.twitter.com/ReUmfa67ln— Mysk 🇨🇦🇩🇪 (@mysk_co) October 12, 2022
The stock iOS apps that leak user data include the Apple Store, Clips, Files, Find My, Health, Maps, Settings, and Wallet. This means that private user information related to health, payment details as well as details about the devices you own within Apple’s ecosystem and their location can be leaked.
Mysk also discovered that VPN apps on Android also behave the same way with Google services as iOS VPN apps do with stock apps.
I know what you’re asking yourself and the answer is YES. Android communicates with Google services outside an active VPN connection, even with the options “Always-on” and “Block Connections without VPN.” I used a Pixel phone running Android 13.
Apple and Google have yet to acknowledge the security researcher’s findings.
Read More: