Microsoft 365 Defender Research Team has disclosed details of a ‘Powerdir’ vulnerability that could have allowed attackers to bypass all macOS’ Transparency, Consent, and Control (TCC) protections and gain unauthorized access to user data. Apple was informed of the vulnerability identified as CVE-2021-30970, which the company resolved in macOS Monterey 12.1 update back in December.
‘Powerdir’ vulnerability fixed by Apple in macOS 12.1
Apple had introduced TCC in macOS Mountain Lion back in 2012, which helps control app access to privacy settings such as camera, microphone, or location, as well as iCloud account, user calendar, contacts, reminders, photos, and more. All these options privacy options can be seen by going to System Preferences > Security & Privacy.
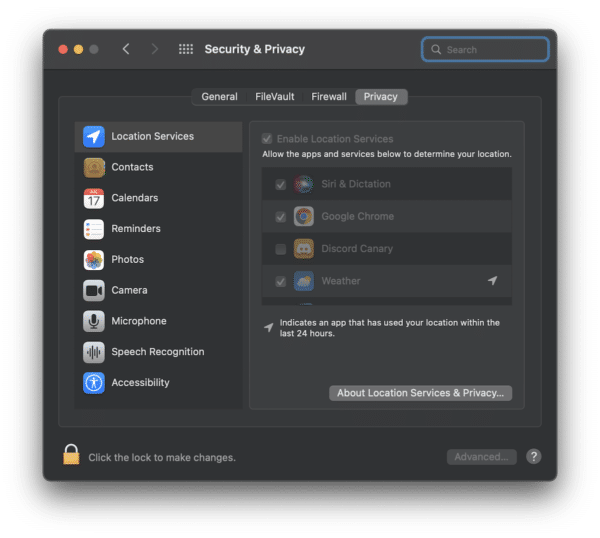
To protect access to these settings, Apple prevents unauthorized code execution and only apps which full disk access can modify them. However, an issue was found by the Microsoft 365 Defender Research Team which meant that hackers could modify the user’s home directory and create a fake TCC database with a history of app requests to fool the system.
We discovered that it is possible to programmatically change a target user’s home directory and plant a fake TCC database, which stores the consent history of app requests. If exploited on unpatched systems, this vulnerability could allow a malicious actor to potentially orchestrate an attack based on the user’s protected personal data.
The potential harm from such a bypass could allow hackers to install malicious apps and even access the microphone or camera without the user’s consent.
For example, the attacker could hijack an app installed on the device—or install their own malicious app—and access the microphone to record private conversations or capture screenshots of sensitive information displayed on the user’s screen.
To give credit where it’s due, the initial proof of concept by the Microsoft 365 Defender Research Team did not work on the new macOS Monterey update, so the team had to modify its POC exploit to get it to work on macOS 12.0, hence confirming the adage that security is a cat and mouse game.
You can read more details on the exploit on the Microsoft 365 Defender Research Team blog. Make sure to update to macOS 12.1, if you have not yet already, to stay safe from the exploit.