Facebook has taken action against a group of hackers that were using its social media platform to spread malware on iOS and Android. The malware was found to be used for spying on the Uyghur community in China through its privileged access.
As per Facebook, the malware was infecting people based on their location, devices, browsers, and language settings, rather than blinding infecting all users. It was also being disguised as actual news websites, which would allow it to infect targeted devices. Facebook also notes that fake profiles on social media, and fake third-party app stores were being used to spread the malware.

Facebook shares details of malware that was spread through its platform
Many apps posing as keyboards, religious apps, and prayer apps, were being used to infect users. As per Facebook, the malware was being spread by sharing links to websites infected by the malware, rather than directs links to the malware itself.
This activity had the hallmarks of a well-resourced and persistent operation while obfuscating who’s behind it. On our platform, this cyber espionage campaign manifested primarily in sending links to malicious websites rather than direct sharing of the malware itself. We saw this activity slow down at various times, likely in response to our and other companies’ actions to disrupt their activity.
The fake websites had malicious JavaScript in them, which would infect target devices by exploiting a bunch of vulnerabilities to install malware known as Insomnia. A number of these zero-day hacks affected iOS versions 10 – iOS 12.3.2, however, these exploits were fixed in later updates by Apple. Insomnia was able to access the target devices’ contact and location data, as well as information from apps like Messages, WhatsApp, Gmail, Telegram, and more.
Cybersecurity company Volexity explained how Insomnia works using the below diagram.
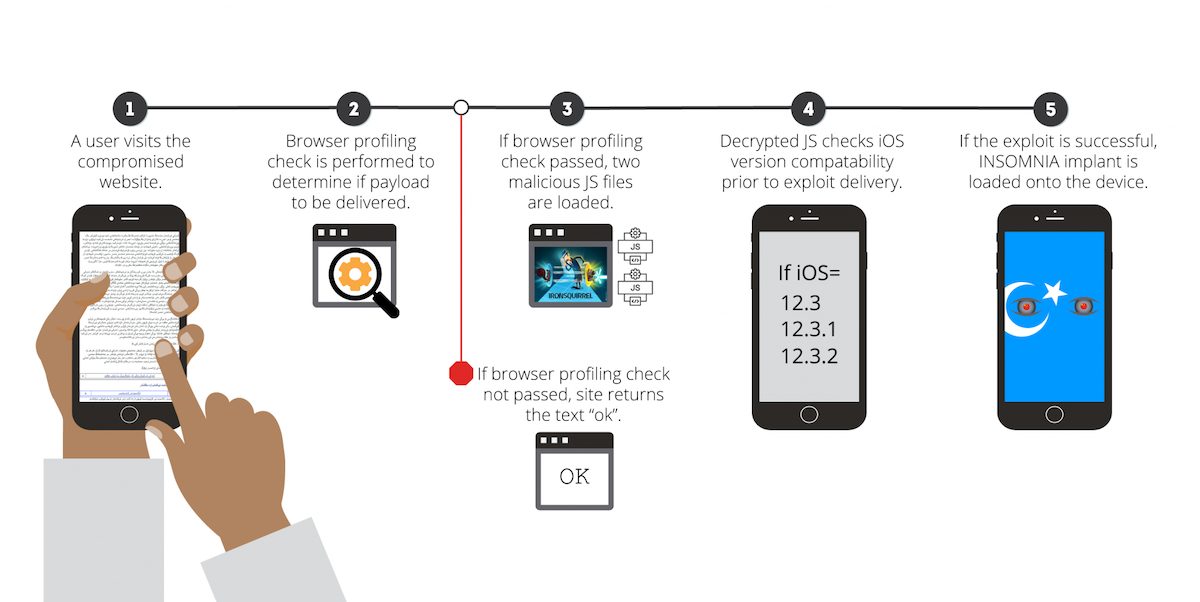
On Android, the infection was done through fake apps or websites that acted as fake app stores and apps themselves. Due to the simple toggle that allows users to install third-party apps, the hackers were able to use social engineering to convince users to install these apps and give them the necessary permissions to steal their data.
These hacks were not only advanced enough to infect devices and steal user data, they were also able to stay hidden for a long time because of the multiple checks they had in place for infecting targets.
via ArsTechnica

1 comment